UberEther Hosts Presentation to Show Federal CISOs and CIOs How to Enable the Baseline of a ZeroTrust Architecture Without Replacing Decades of Existing Infrastructure
Sterling, VA: June 18, 2021 – In case there was any doubt about whether the Federal Government was moving toward ZeroTrust, the recent Executive Order on Improving the Nation’s Cybersecurity and DoD Zero Trust Reference Architecture have provided guidance for when and how Federal Civilian and Defense agencies must implement it. For Chief Information Security Officers (CISOs) already managing complex digital transformation initiatives, how to implement ZeroTrust without overhauling all existing infrastructure is top of mind. Is it even possible to enable the baseline of a ZeroTrust architecture without replacing decades of existing infrastructure?
The answer is Yes. Yet, the reality is agencies have too much data for most policy engines to read and evaluate in real-time, said Matt Topper, UberEther Founder.
“Much of this data is buried within the Security Information and Event Management systems but not made available for use across the enterprise. At the same time, most Security Operations Centers (SOCs) have no visibility into the business context of the users they are investigating, and so end up performing a shot gun approach to security that leads to chasing people who are working within the scope of their mission, and sometimes bypassing malicious actors in the process,” said Topper.
Layering Operational Intelligence with Identity Management to Provide the Baseline for Trust
Identity management is the first line of defense in securing government data and systems. Security operations teams look at what is happening minute by minute to hunt down anything that looks suspicious.
“They’re hunting, but they don’t know if they’re hunting a squirrel, a deer, or a polar bear. This happens because most security information and event management systems do not layer in the business context to consider why a user (or app) is accessing specific data. I call it business blind,” said Topper.
By layering the business context over the log data, UberEther helps analysts and CISOs access the intelligence to know what they’re hunting… and how to hunt it. Topper says it’s like SEIM on steroids.
Learn About SEIM on Steroids
Join UberEther founder Matt Topper and Senior Architect Matt Volo for User Behavior Analytics: Marrying Identity and the SOC Like Peanut Butter and Jelly, June 23, 1 to 2:00 p.m. EDT at Identiverse 2021.
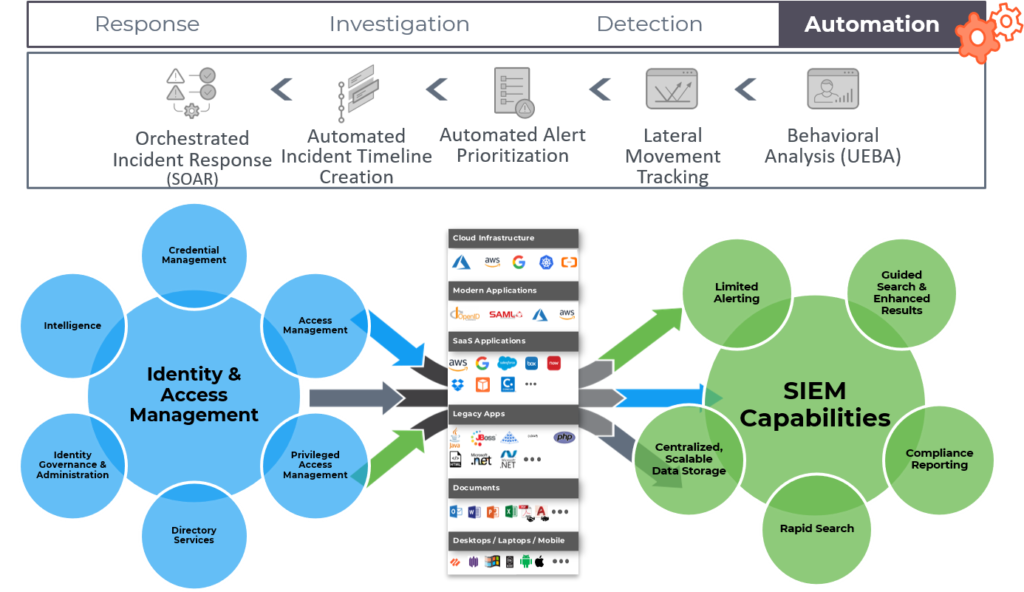
Together they will discuss how UberEther uses User Behavior Analytics to bridge the SOC and identity teams to build a Trust foundation for all an agency’s users, systems, and devices. Through this process, UberEther is able to distill volumes of distributed data into actionable risk scores used across policy decision points and identity governance workflows. This data goes back into the SOC to allow the team to quickly execute targeted playbooks when alerts are triggered.
This presentation will also cover what is next for user behavior analytics and how the emerging Continuous Access Evaluation Protocol (CAEP) will allow agencies to provide deeper dynamic access authorizations for federated identities.
Details:
Event: User Behavior Analytics: Marrying Identity and the SOC Like Peanut Butter and Jelly
Date: June 23, 1:00 p.m. to 2:00 p.m. EDT (11:00 a.m. to noon MDT).
Location: Virtual
Register: https://uberether.com/ueba/
About UberEther
The perimeter is no longer the enterprise network firewall, but the identity of every person or device accessing corporate workloads and data. UberEther is a full stack technology integrator that builds innovative solutions for government clients and turns their security and access control needs into a value-added enabler that transforms the organization in ways previously not possible.
We are a Virginia Corporation based in Sterling, VA. Awards include: DHS HQ First Federal Risk and Authorization Management Program (FedRAMP) High Platform Deployed to AWS, DHS HQ First FISMA High GSS Cloud Platform, ExaBeam Innovation Partner of the Year. UberEther is working toward FedRAMP of High Authority to Operate (ATO) for their Integrated Managed Identity Platform. GSA Schedule 70, Item Numbers 132-51 – Information Technology Professional Services; 132-51 ST / LOC; 132-51 ARRA. For more information, email hello@uberether.com.