In the ever-evolving cybersecurity landscape, the recent Microsoft key compromise incident is a stark reminder of the importance of customer-controlled encryption keys and SaaS tenant log transparency. This incident, attributed to the Chinese threat actor Storm-0558, involved the acquisition of a private encryption key (MSA key) and its use to forge access tokens for various Microsoft and Azure services.
The Power of Encryption Keys
Encryption keys, particularly those of identity providers, are among the most potent secrets in the digital world. Their compromise can lead to unauthorized access to a multitude of services, from email boxes to cloud accounts. In the Microsoft incident, the compromised MSA key was not limited to Outlook.com and Exchange Online, as initially assumed. It allowed the threat actor to forge access tokens for multiple types of Azure Active Directory applications, including SharePoint, Teams, OneDrive, and any customer applications that support the “login with Microsoft” functionality.
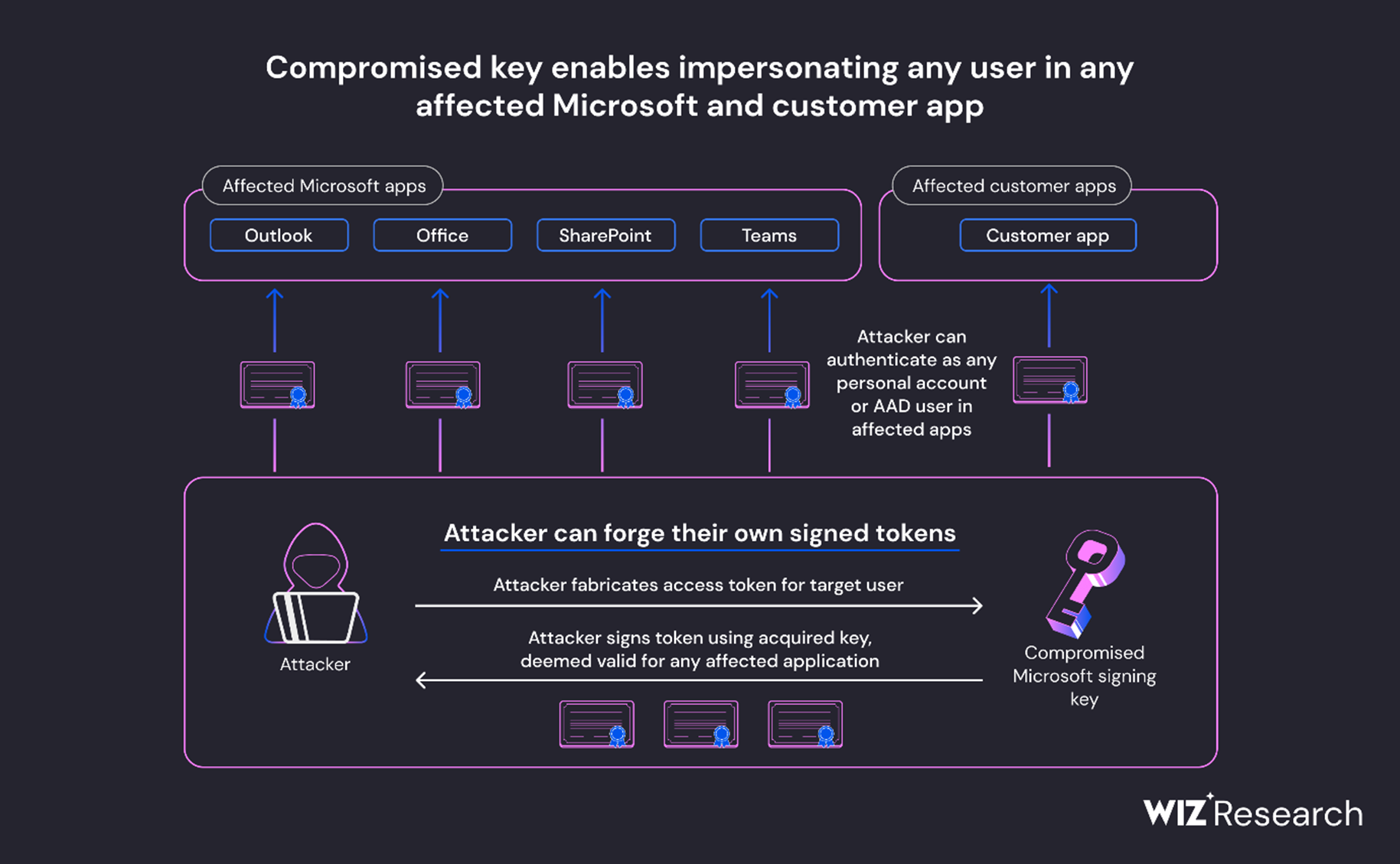
This incident underscores customers’ need for control over their encryption keys. This compromise was so impactful because federation between tenants is designed to be easy between EntraID (AzureAD) customers. Microsoft depends on a small number of public keys for its SaaS applications.
By managing their own keys, customers can ensure they are securely stored and appropriately rotated, reducing the risk of compromise. While many vendors provide options for customer-managed keys for data encryption, very few support it for customer identity providers—moreover, even fewer support allowlists for the sources for these keys. These attacks have become more popular after the 2020 SolarWinds supply chain hacks. Over three years later, we’re seeing major vendors compromised through the same approaches over and over again.
The Need for Log Transparency
The Microsoft key compromise also highlighted the importance of log transparency. While Microsoft mitigated the risk by revoking the impacted encryption key and publishing attacker IOCs, it was difficult for customers to detect the use of forged tokens due to a lack of logs on crucial fields related to the token verification process. Only customer accounts with an E5 license were previously privileged enough to get access to the necessary logs
Log transparency is crucial for customers to monitor their applications and detect unauthorized access. It allows customers to track who accessed what data and when providing a clear audit trail that can be used to detect and respond to security incidents promptly. Luckily, Microsoft is moving to reduce the level at which these logs become transparent to their customers.
How the UberEther Advantage Platforms are Built Different
In the wake of this incident, it’s clear that the industry, especially cloud service providers, must commit to a higher level of security and transparency. They need to ensure the protection of critical keys and provide customers with the necessary tools and visibility to secure their applications.
Both of these features have been a core security design decision in our IAM Advantage and ATO Advantage platforms. Multi-tenant designs where shared encryption and signing keys are used are inherently less secure. At UberEther, we go one step further, and utilize a private tenant design. While more expensive to operate, it allows our customers to ensure everything within their boundary is encrypted and secured with the keys they control to protect their applications and data within our hosted services.
boundary is encrypted and secured with the keys they control to protect their applications and data within our hosted services.
Similarly, every single log generated within the boundary from the infrastructure, to the platform, to the software running within is provided back to the customers with full transparency. We provide this through each customer’s SIEM dashboards and into an archive location where the customer can pull that data in directly to their own enterprise SIEMs.
Having built solutions for nearly 20 years supporting the United State Intelligence Community, the Department of Defense and Homeland Security, we know how to engineer secure systems. However, we also know that securing services from the world’s most well funded actors is a collective game. We realize we are a small business, but also know that we can hone into identity based indicators of compromise better than most because this is our core focus.
With more and more of an organization’s trust being developed around their Identity Provider and the federated trusts managed within, it’s imperative that organizations look to stronger and stronger controls being enforced first at authentication time, and then on subsequent authorization requests. It’s the whole reason these platforms were developed for our customers.
Conclusion
The Microsoft key compromise incident serves as a stark reminder of the importance of customer-controlled encryption keys and SaaS tenant log transparency. As we continue to rely on cloud services, it’s crucial that we learn from such incidents and take the necessary steps to secure our applications and data. UberEther’s Advantage Platforms, with their emphasis on customer-controlled encryption keys and log transparency, offer a robust solution to these challenges.
Stay tuned to this space, as we will be announcing soon how we are taking these concepts to the next level to protect more of your infrastructure and services through guaranteed and attested transparency.
